This article offers practical tips and tools to protect your private information while shopping online, emphasizing cautious browsing and privacy-enhancing tools. Using strategies like alias emails, virtual payment cards, VPNs, and privacy-focused browsers can significantly reduce the risk of data theft and tracking. #DigitalFingerprinting #PrivacyTools
Tag: SPAM

This article discusses how context augmentation can significantly improve the effectiveness of Large Language Models (LLMs) like ChatGPT in bug bounty hunting. It emphasizes the use of external information to enhance recon, vulnerability chaining, and reporting, transforming LLMs into smart security assistants. #BugBounty #ContextAugmentation

Cybersecurity researchers have uncovered TokenBreak, an attack that exploits tokenization strategies to bypass content moderation in large language models with minimal changes to input text. This technique can lead to prompt injection and security vulnerabilities, especially against models using BPE or WordPiece tokenization. #TokenBreak #LLMsafety…

A large-scale campaign is compromising legitimate websites by injecting obfuscated JavaScript using the JSFireTruck technique, redirecting users from search engines to malicious pages that deliver malware and unwanted content. The campaign affects hundreds of thousands of webpages and employs type coercion-based obfuscation, making detection and analysis challenging. #JSFireTruck #Unit42 #VirusTotal…

Cybercriminals tied to the Black Basta ransomware operation are evolving their tactics, using email bombing, Teams phishing, and Python scripts to gain persistent access to networks. The threat landscape is shifting as former affiliates potentially migrate to other ransomware groups like CACTUS or BlackLock, while new malware and attack strategies emerge….

The ransomware group Black Basta disbanded after internal chat leaks, but its tactics, especially mass email spam and Microsoft Teams phishing, continue to be used by former members and new groups. Emerging attack methods now include Python script execution with cURL for payload delivery, emphasizing the need for strong user education and vigilant defense strategies. #BlackBasta #MicrosoftTeamsPhishing #CactusRaaS
The Black Basta ransomware group’s social engineering attacks sharply declined after December 2024, with evidence indicating that BlackSuit affiliates have adopted or absorbed their tactics. Rapid7’s analysis reveals sophisticated Java RAT and QEMU-based malware deployments, leveraging cloud services for command and control, and highlights ongoing evolution in attacker methods. #BlackBasta #BlackSuit #JavaRAT

OpenAI announced the shutdown of ChatGPT accounts linked to Russian-speaking threat actors and Chinese nation-state hacking groups, exploiting AI for malware development, social media automation, research, and cyber campaigns. These groups used the models for developing malware, bypassing security, and executing disinformation and espionage activities. #ScopeCreep #UNC2630 #APT15 #CyberThreatActors…

Cybercriminals have begun using SVG files containing malicious JavaScript in phishing emails to bypass security filters and steal Microsoft 365 credentials. The attack redirects victims to a fake login page via a phishing URL embedded in the SVG file, potentially compromising corporate networks. #SVGPhishing #Microsoft365 #MutationObserver

The imad213 Python-based credential harvester poses as an Instagram growth tool to steal user credentials and broadcast them to multiple malicious bot services. The attacker maintains remote control via a Netlify-hosted kill switch and operates a coordinated network of phishing websites targeting various social media platforms. #imad213 #IMAD-213 #takipcimx #InstagramGrowthTool

Cybersecurity researchers warn about a new ClickFix malware campaign targeting macOS users with social engineering tactics to install Atomic macOS Stealer (AMOS). The attack involves fake Spectrum impersonation sites and malicious shell scripts that deceive users into revealing passwords, leading to data theft and lateral movement. #ClickFix #AtomicStealer…

Symantec’s investigation reveals that many Chrome extensions contain hardcoded API keys and secrets, risking data breaches and unauthorized access for over 21 million users. Protecting sensitive credentials is crucial to avoid exploitation, financial loss, and damage to reputation. #ChromeExtensions #APISecrets…

Symantec’s investigation reveals that many Chrome Web Store extensions contain hardcoded API keys and secrets, exposing over 21 million users to security risks. These embedded credentials could allow attackers to manipulate data, access sensitive systems, and cause financial or reputational damage. #GoogleAnalytics4 #AzureAPI #AWSAccessKeys #GmailAPI #TenorGIF…
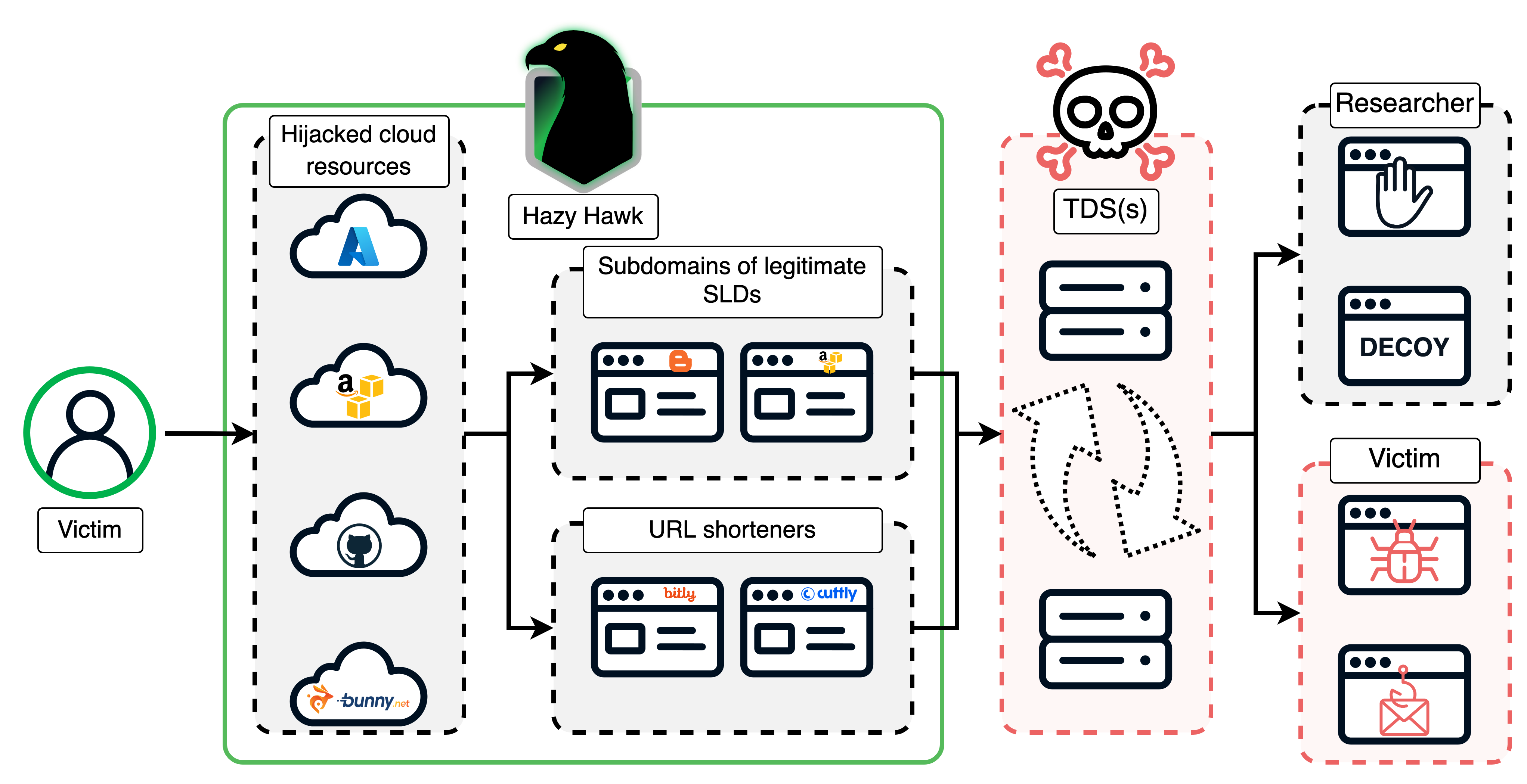
Hazy Hawk is a sophisticated threat actor that hijacks abandoned cloud resources belonging to high-profile organizations by exploiting DNS misconfigurations, primarily dangling CNAME records. Their hijacked domains are used to host malicious URLs that redirect users to scams and malware through complex traffic distribution systems. #HazyHawk #DNSHijacking #CloudResourceHijacking #CDC #jsorg

This article discusses how to detect suspicious traffic using Wazuh and Suricata, focusing on a simulated phishing attack involving Google Calendar invites. It emphasizes the importance of early detection and real-time response tools like Slack alerts to prevent serious security breaches. #LivingOffTheLandBinaries #C2Server