Cock.li, a privacy-focused email provider, experienced a data breach exposing over a million user records through a vulnerability in its now-retired Roundcube platform. The breach highlights the importance of secure webmail configurations, especially for platforms favored by security and cybercriminal communities. #Roundcube #CVE-2021-44026
Tag: SMTP

Malicious open source packages targeting blockchain developers are increasingly used to steal cryptowallet credentials, drain funds, mine cryptocurrency, and hijack clipboard data. Threat actors, including nation-state groups, exploit supply chain vulnerabilities in registries like npm and PyPI, impacting ecosystems such as Ethereum, Solana, TRON, and TON. #ContagiousInterview #BeaverTail #InvisibleFerret #XMRig #ClipboardHijackers
Adversary-in-the-Middle (AitM) phishing attacks increasingly target Microsoft 365 and Google accounts, leveraging sophisticated phishing kits offered as Phishing-as-a-Service (PhaaS). These kits harvest session cookies to bypass multi-factor authentication, facilitating financial fraud and Business Email Compromise (BEC) attacks. #Tycoon2FA #Storm1167 #EvilProxy #SekoiaTDR

Rare Werewolf, an APT group, has targeted Russia and CIS countries using legitimate software and phishing tactics to deploy cryptojackers and facilitate remote access. The group’s activities include using PowerShell scripts, remote desktop tools, and decoy documents, complicating detection efforts. #RareWerewolf #APT #Cryptojacking…

Librarian Ghouls, an APT group targeting Russian and CIS entities, employs legitimate third-party software and scripting rather than custom malware for its attacks, focusing on credential theft and deploying a crypto miner. Their ongoing campaign features phishing emails, remote access tools, and complex infection stages, with hundreds of victims primarily in Russia and neighboring countries. #LibrarianGhouls #RareWerewolf #Rezet #XMRig #AnyDesk

Cybersecurity researchers have identified a supply chain attack involving multiple npm packages associated with GlueStack, delivering malware capable of remote system control. Similar malicious activity targeting npm and PyPI packages indicates coordinated efforts by threat actors, with potential widespread impact. #GlueStack #npmMalware…

Two malicious npm packages, express-api-sync and system-health-sync-api, contain backdoors designed to wipe out entire production environments when triggered. These packages use hidden endpoints, cross-platform destruction commands, and covert email communication channels to gather intelligence and execute system destruction. #express-api-sync #system-health-sync-api #botsailer #npm

Cybersecurity experts have identified a new Linux cryptojacking campaign called RedisRaider, which targets publicly accessible Redis servers to deploy cryptocurrency miners. This threat impacts Linux server infrastructures and Redis instances globally. #Redis #LinuxServers…

ModiLoader (DBatLoader) malware is distributed via phishing emails impersonating a Turkish bank, ultimately deploying SnakeKeylogger to steal sensitive information through various exfiltration methods such as email, FTP, SMTP, and Telegram. The malware uses sophisticated evasion techniques, including DLL side-loading and process injection, to avoid detection and maintain persistence on infected systems….

Horabot is a sophisticated malware campaign targeting Spanish-speaking Microsoft Windows users through phishing emails that impersonate invoices and deliver malicious HTML attachments. It steals sensitive information including email credentials and contact lists, spreads via Outlook automation, and installs banking trojans, impacting Microsoft Windows and Outlook environments. #MicrosoftWindows #Outlook

Threat actors are increasingly weaponizing benign open source packages by employing techniques like typosquatting, obfuscation, and multi-stage malware to infiltrate software supply chains and remain undetected. These evolving tactics significantly impact developer ecosystems and software supply chains such as npm, PyPI, and Go Module. #npm #PyPI #GoModule
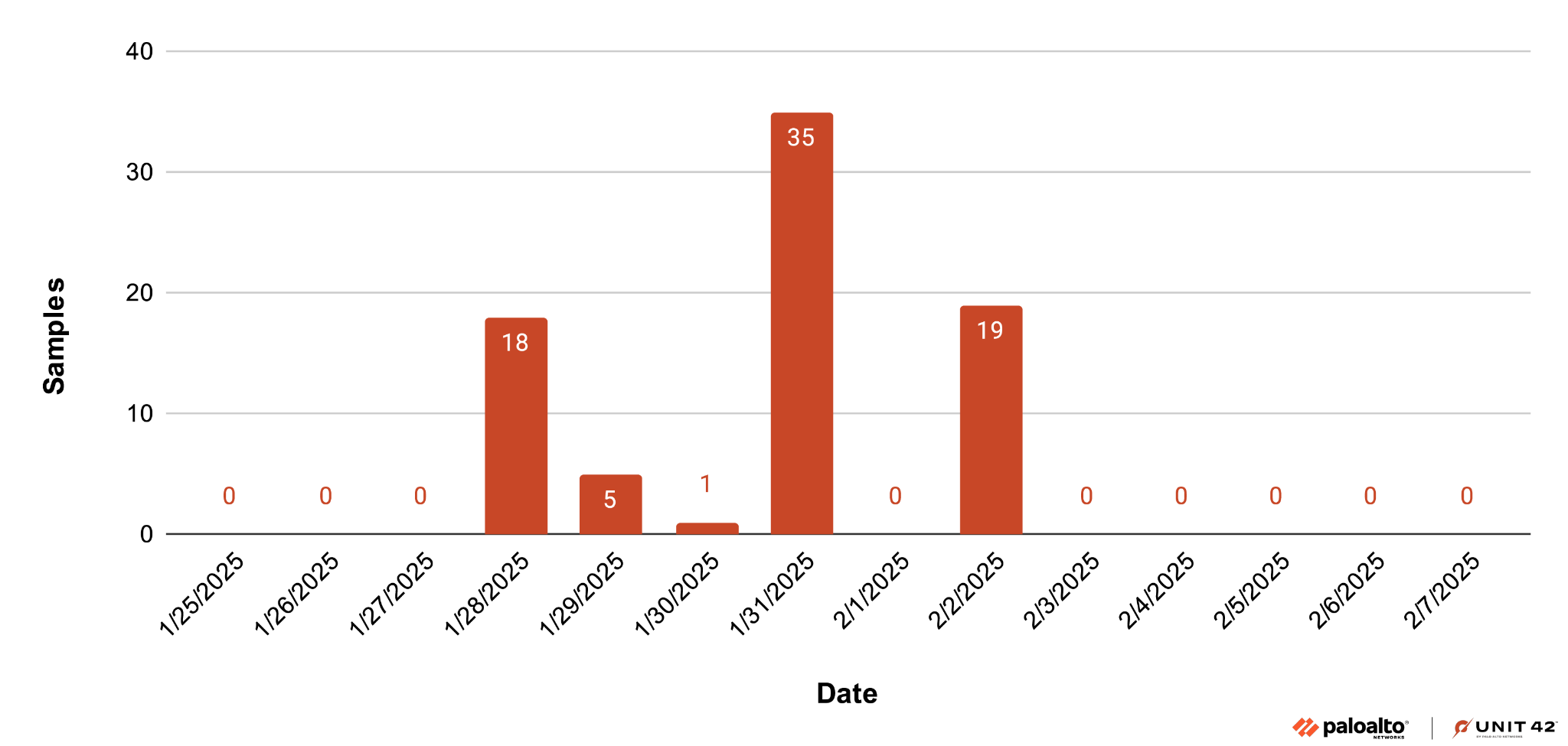
Unit 42 researchers discovered a new variant of DarkCloud Stealer malware in early 2025, leveraging AutoIt compiled executables and multi-stage attack chains delivered via phishing emails and file-sharing services. This evolving campaign employs obfuscation and anti-analysis techniques to steal sensitive data including browser credentials, email passwords, and FTP logins, significantly impacting…

A targeted campaign exploited Microsoft Entra ID’s legacy authentication protocol BAV2ROPC, allowing attackers to bypass MFA and gain unauthorized access to admin accounts across finance, healthcare, and tech sectors….


