This week’s cybersecurity updates highlight ongoing threats, including the BadBox 2 botnet targeting IoT devices and fraud associated with Hedera Hashgraph NFTs. Major organizations like the FBI, NSO Group, and Microsoft announced actions and initiatives to combat cyber threats and improve security resilience. #BadBox2 #NSOGroup #HederaHashgraph #CISA #MicrosoftEuropeanSecurity…
Tag: COLLECTION

Two malicious npm packages, express-api-sync and system-health-sync-api, contain backdoors designed to wipe out entire production environments when triggered. These packages use hidden endpoints, cross-platform destruction commands, and covert email communication channels to gather intelligence and execute system destruction. #express-api-sync #system-health-sync-api #botsailer #npm

This article provides a comprehensive pentesting roadmap for aspiring ethical hackers, emphasizing hands-on labs like Hack The Box retired machines and Pro Labs. It highlights the importance of structured practice, following curated lists like the TJ Null List, and copying walkthroughs to gain real-world skills. #HackTheBox #TJNullList

In 2024, ESET researchers identified BladedFeline, an Iran-aligned APT group active since 2017, targeting Kurdish and Iraqi government officials with advanced malware including the Whisper backdoor and PrimeCache IIS module. The group is assessed as a subgroup of OilRig, utilizing sophisticated tools and maintaining long-term access for cyberespionage purposes. #BladedFeline #Whisper #PrimeCache #OilRig

Infostealers have become a significant cyber threat, accounting for almost a quarter of all incidents detected by Huntress in 2024, by harvesting sensitive credentials and data that fuel ransomware, extortion, and identity theft attacks. The evolution of infostealers, their targeting of diverse information including corporate credentials and cloud keys, and the law enforcement takedowns of related marketplaces highlight both the risks and ongoing efforts to combat these threats. #Infostealers #LummaStealer #RedLine #BansheeStealer

DuplexSpy RAT is a multifunctional remote access trojan with advanced capabilities including surveillance, persistence, and stealth through fileless execution and privilege escalation. Despite being released for educational purposes, its modular design and open-source availability pose significant risks of malicious exploitation. #DuplexSpyRAT #ISSAC #WindowsUpdate

Bitter is a state-backed hacking group believed to be operating on behalf of Indian intelligence, focusing on espionage against government and diplomatic targets. Their operations include spear-phishing, malware deployment, and targeted campaigns across South Asia and expanding to other regions like Turkey. #Bitter #APT-C-08 #IndianGovernment #Espionage #ThreatActors…

Ukrainian police and Europol have arrested a man accused of hacking into over 5,000 user accounts of an international hosting provider to conduct illegal cryptocurrency mining, resulting in $4.5 million in losses. The suspect, active since 2018, used malicious tools and maintained multiple accounts on hacker forums, evading detection by frequently…

The FTC is committed to strengthening online privacy protections for children by enforcing new rules and urging Congress to update existing laws. The agency emphasizes the need for more effective age verification methods and greater parental control to protect children’s personal data online. #COPPA #ChildrensOnlinePrivacy…

TA397 is a state-backed espionage group likely operating on behalf of the Indian state, targeting government and defense organizations primarily in Europe and Asia with interests in China and neighboring countries. The group uses spearphishing emails, scheduled tasks, and various malware payloads to conduct intelligence gathering, exhibiting consistent infrastructure activity within…

Vanta is a tool that automates cybersecurity compliance by integrating with your tech stack and mapping systems to over 35 security frameworks like SOX 2, ISO 27001, and GDPR. It streamlines evidence gathering, risk management, and policy tracking, reducing manual effort and improving security posture. #GDPR #ISO27001

A recent investigation uncovered over 100 backdoored GitHub repositories masquerading as malware and gaming cheats, with infection chains leading to multiple RATs and infostealers. The campaign primarily targets cheating gamers and inexperienced cybercriminals but poses risks to anyone compiling unverified code. #SakuraRAT #ischhfd83 #SearchFilter

A group of malicious GitHub repositories are distributing hidden backdoors and malware, targeting hackers, gamers, and researchers with fake exploits, game cheats, and remote access tools like Sakura RAT. Sophos researchers uncovered a coordinated campaign involving automated commits and obfuscated payloads designed to infect devices and steal data. #SakuraRAT #GitHubBackdoors

Multiple malicious packages in npm, Python, and Ruby repositories are exploiting supply chain vulnerabilities to steal cryptocurrency funds, exfiltrate data, and delete codebases. These threats leverage geopolitical events, typosquatting, and AI model abuse to infect development environments and targets worldwide. #Fastlane #PyPI #cryptocurrencyheist…
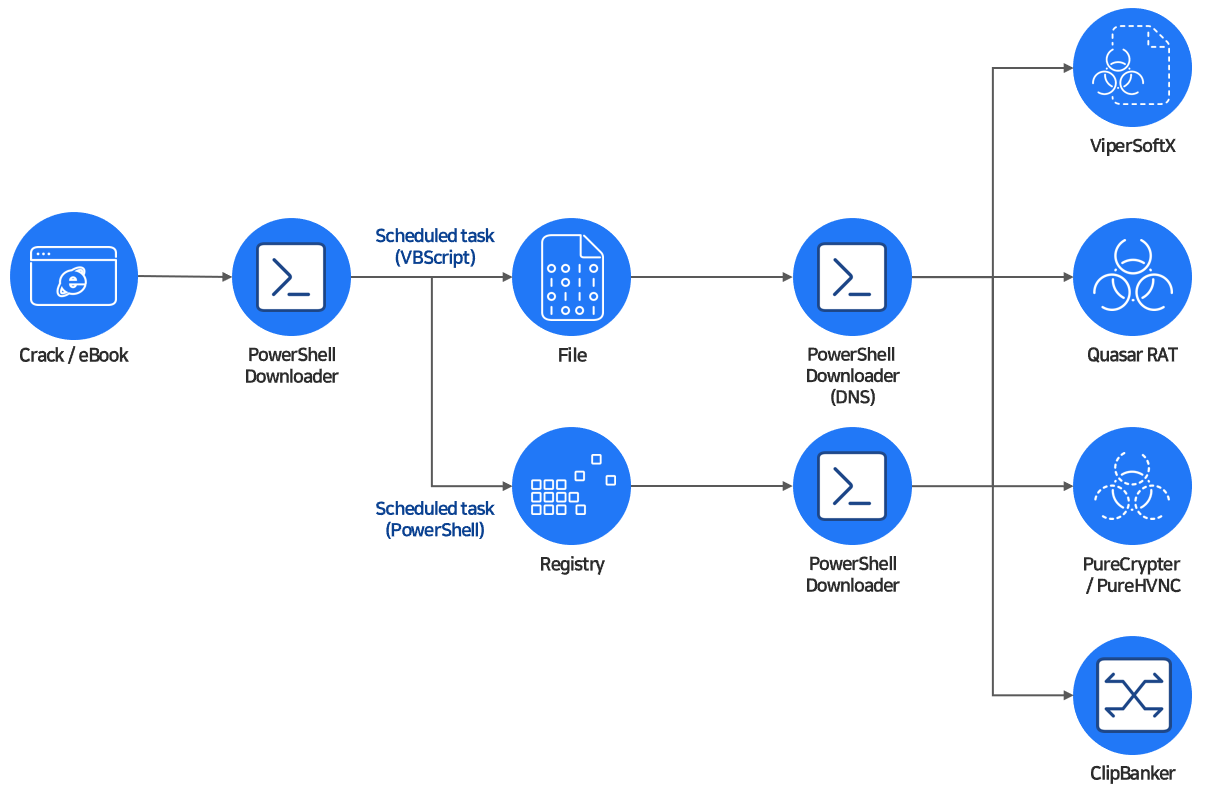
The ViperSoftX threat actor continues to distribute malware targeting cryptocurrency users, employing PowerShell scripts to install remote access tools and steal sensitive wallet information. The malware uses various infection methods, including disguised illegal software, and implements clipboard monitoring to capture cryptocurrency-related data. #ViperSoftX #QuasarRAT #PureCrypter #PureHVNC #ClipBanker…
